Security
The security properties section contains information related to the user's status, the licenses of the products they have installed in the environment, their access permissions, the roles they are part of, and two-factor authentication, if they have chosen to implement it.
An asterisk*on the label indicates that the property is required.
Properties
State and Expiration
User State
Indicates if the user is active or not.
An inactive user cannot enter the environment as their account is deactivated.
Expiration Date
The user account is automatically deactivated when the date entered in this property is reached. This automatic deactivation does not use the tasks delegations scheme.
This property can be used when the authentication of users is performed by Deyel.
Failed Accesses
Displays the number of failed accesses due to incorrect password.
It is incremented every time user authentication fails due to an incorrect password and returns to zero when the user authenticates successfully.
When the user exceeds the Maximum number of failed accesses their account is locked.
Lockout Date
Displays the date and time when the user's account is locked.
It is used to control the Maximum lockout time of the user’s account.
Licenses
Each environment of Deyel has use licenses that enable the use of licensed applications during a period of time and by a certain number of users.
In this section the list of licensed application the user can use is indicated and which type of user license they have assigned to do this.
Product
Indicates the licensed application the user can use.
License Type
Indicates the type of user license that is assigned to the user to use the product.
When the use of double authentication factor is enabled in the environment, this section is visualized.
If the Two Step Authentication configurable property is set to “Optional”, the user can decide whether to use 2FA to authenticate. On the other hand, if the value is "Mandatory", the user must configure the use of 2FA. When the user is authenticated for the first time, Deyel sends a first TOTP code by email and in turn generates an account recovery code.
For security, to prevent improper access to this information by an unauthorized person, the user is required to confirm his identity by entering his password correctly to display this information.
Enable Two Step Authentication
The user can enable or disable the use of 2FA. If it is enabled, it indicates how they want to receive the TOTP codes, being able to choose any of the following options:
Send Codes to my Mailbox
If this option is selected Deyel sends the access codes to the user's email account, which has been reported in the profile.
Use Google Authenticator
If the use of the Google authenticator is selected, a panel is displayed that tells the user how to configure such application.
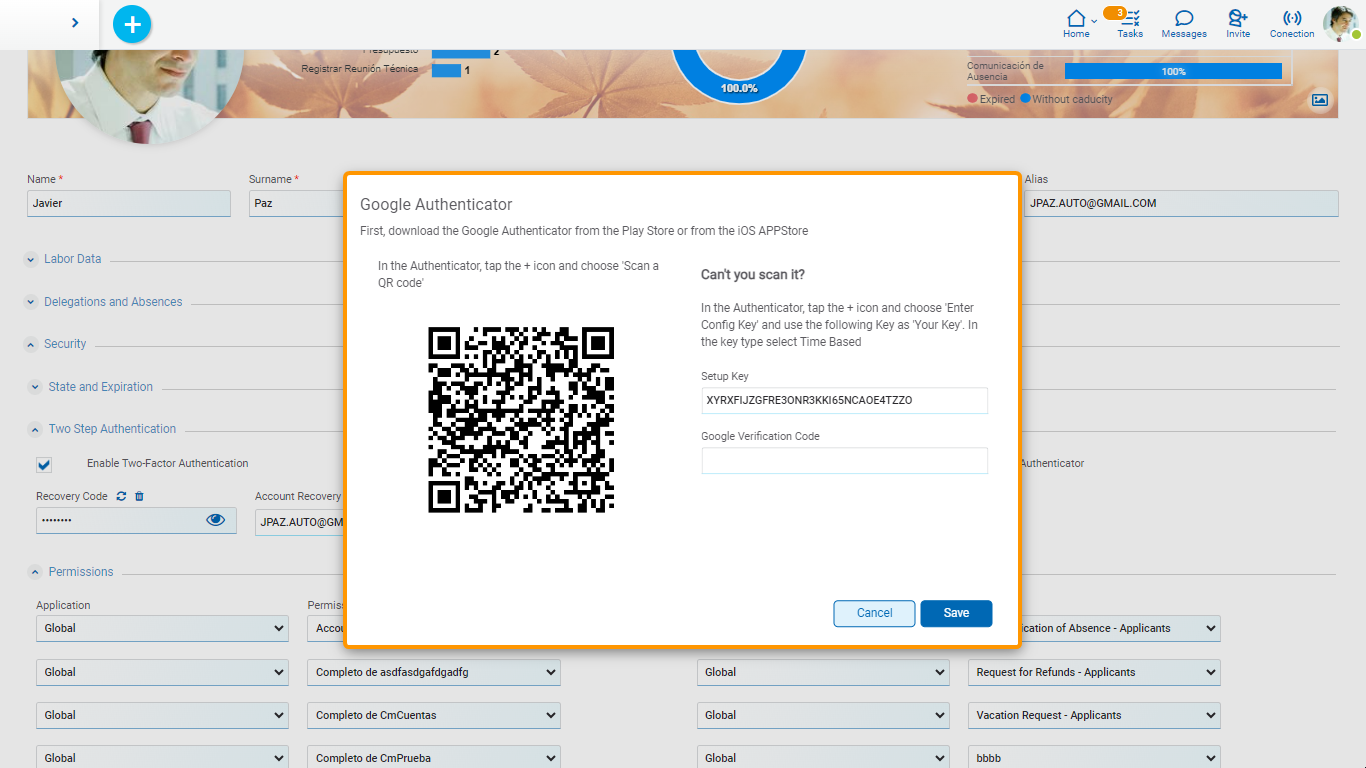
A QR code can be scanned or enter a key that is generated by Deyel.
The user must follow the indicated steps and to confirm that they have correctly installed and configured the authenticator, they are asked to enter a TOTP code generated by that application. Only when the code is verified correctly it is possible to save the use configuration of the authenticator.
When the authenticator has been configured and is in use, a configuration icon is displayed next to the field. By clicking, the same panel that allows to configure the use of the application on the same or another device is accessed.
The security administrator cannot access a user's 2FA settings. They can only disable 2FA to contemplate particular situations but not re-enable it, only the user himself can do it.
Recovery Code
When the user cannot complete their two-step authentication because they do not receive their TOPT verification codes, it is necessary to offer a mechanism that allows them to overcome this inconvenience, using a recovery code.
When the user activates 2FA, a recovery code is generated. that can be consulted only by the user himself. To visualize the value, the icon ![]() must be used.
must be used.
The icon ![]() allows to generate a new recovery code, the previous one is no longer valid.
allows to generate a new recovery code, the previous one is no longer valid.
The icon ![]() allows to remove the recovery code, indicating that this mechanism is not going to be used.
allows to remove the recovery code, indicating that this mechanism is not going to be used.
On the home page, when the user needs to pass 2FA, they can request access with this recovery code.
If the correct code is reported, the 2FA is validated and the user can enter.
Account Recovery Email
When the user does not receive the TOTP verification codes and also does not remember his recovery code, another mechanism is provided for him to receive the access codes.
The user can optionally register an alternative email address, which must be different from their institutional account.
To verify that the user has access to the email account, an email is sent to that address, containing a TOPT validation code that must be entered in an attached field.
When accept is pressed and there was some change in the recovery email, it is verified that the code is valid. Otherwise, it is not allowed to register the indicated email account.
Permissions
The access permissions the user has assigned are listed. Each element from the list indicates the name of the permission and the application they belong to.
In the first positions the permissions the user inherits for belonging to an organizational unit, to a role or to a job position are displayed. These elements are displayed protected and it is not possible to delete them from the list. Hovering over each of these elements, it is displayed from which object the permission is inherited.
Following the inherited permissions, the permissions assigned directly to the user are shown. When creating or modifying the user the elements from the list can be added or deleted.
First the application is selected and then the permission of such application to be assigned to the user is selected.
When permissions from a licensed application are assigned, this one must be able to be used by the user. If the application is not available in the use license of the environment, the permission is protected and it is possible to delete it from the permissions list, but not modify the element.
The permission "Account Manager" can only be assigned to a unique user.
In On-Premise installations of Deyel, this permission can be assigned or removed from a user by the security administrator.
In Cloud installations, the site of Deyel must be used to change the user defined as "Account Manager".
In every installation there exists a set of predefined permissions that can be assigned to the users.
Roles
The roles the user performs are listed. The list is dynamically conformed when accessing the user profile, recovering the roles where the user or their organizational unit are actors. Each element indicates the role name and the application it belongs to.
In the first positions the roles the user inherits for belonging to a unit are displayed and then the roles where the user is an actor.




