Users
Every person using Deyel or any of its applications based on this platform are called users. As such, they have a code that uniquely identifies them, an access key which allows them to authenticate and initiate the work session and a user profile, that collects their personal information, working information, their preferences, additional data, etc.
There is a type of user that does not represent a person, called "Smart Thing". It is about devices, virtual or physical, that have the capacity of communicating with other devices, reacting to events and executing specific functions. Smart things can participate of the business processes, as initiators of such or as responsible users of executing activities, so as to optimize the execution of such processes. For example, the execution of daily tasks or calculus tasks can be delegated to them.
Smart Thing
Chatbots
Among the users of type "Smart Thing" there exists a specific type that is the chatbot.
A chatbot can communicate with other users using Tedis, interpreting specific messages. Each chatbot can define a process to model the way in which it responds to each of the messages received. The answer can be simple, for example responding with a predefined sentence, or it can be more complex and shoot the execution of a business process.
Chatbots are defined to interact with users through the messages, delegating this way the execution of tasks. Human users can use the chatbots as their assistants, so that they automate the actions the user wants and reply to their messages.
Rest API Client
Other user of type “Smart Thing” is the Rest API Client.
A Rest API client is used so that the external applications can be integrated with a Deyel environment. To consume the resources exposed in Deyel Rest API it is necessary to send the credentials of such user to do the authentication and generation of the corresponding access token.
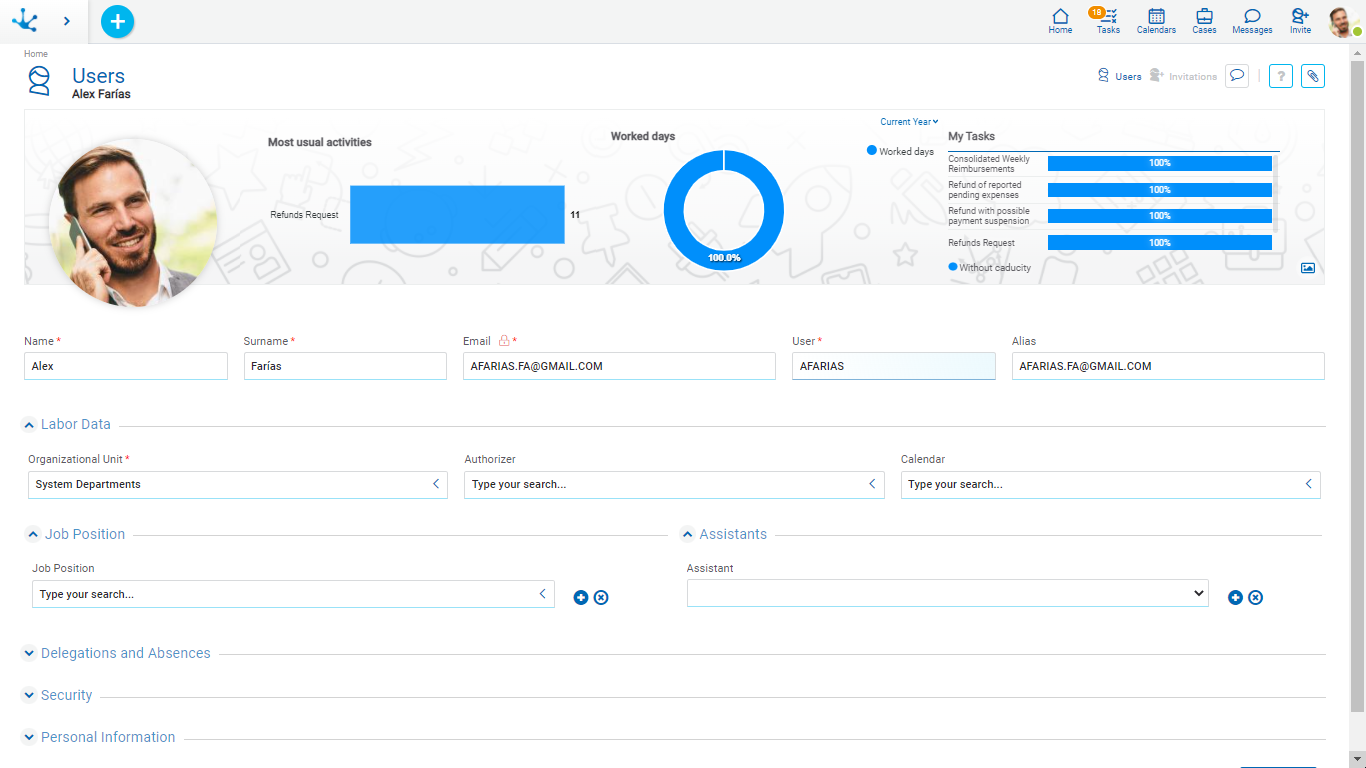
For each user a profile is kept with the following information:
For users of type "Smart Thing", this group of properties must be defined.
An asterisk*on the label indicates that the property is required.
Profile Image
Each user can upload to their profile an image from a file. In case of not informing it, an image with the user´s initials is automatically generated.
User
Code that uniquely identifies the user.
Alias
The value entered in this property works as an alternative code for the user. For example, email address can be used or any other coding that uniquely identifies the user. Deyel checks that there are not two users with the same alias.
When entering the portal, the user can enter either his code or his alias to authenticate.
Behavior Indicators
Information about usual tasks, days worked and the last tasks of the user are graphically displayed.
•With the indicator “Most usual activities” a ranking of the most executed activities is displayed.
•With the indicator “Worked days”, it is seen how was their workplace attendance. When clicking on this indicator, the profile form is displayed so that absences and licenses with their type and period covered are expanded.
•With “My tasks” a summary of the assigned tasks is displayed, together with their state regarding their due date. By clicking on these tasks, the grid of the task with its cases can be displayed.
Cover Image
It can be personalized selecting an image to use as background from the icon  .
.
Name - Surname
These properties may not be informed for smart things.
The value entered in this field works as an alternative code for the user. Deyel checks that there are not two users with the same email.
If a user shows their profile the icon ![]() is displayed to the right of the Email property. When pressing it a field that allows entering the password of the email address is displayed. This configuration is necessary so that the user can do the email sending when using forms.
is displayed to the right of the Email property. When pressing it a field that allows entering the password of the email address is displayed. This configuration is necessary so that the user can do the email sending when using forms.
Organizational Unit
Indicates the organizational unit in which the user works.
Indicates the one in charge of authorizing or approving the processes started by the user.
It is an optional property, that makes reference to another user belonging to the same organizational unit or to a different one.
This property can be recovered from the business processes so as to set the participant responsible to those activities that require an authorization, by using an agent Authorizer.
Calendar
Identifies the calendar that establishes the dates and working hours of the user.
This property can be defined for each user individually.
When the user has not a special calendar defined, then the current calendar at the level of the organizational unit to which they belong is considered. If there is no definition of a calendar in such unit, it is sought at the higher levels of the organizational structure, until detecting the calendar to apply.
The root organizational unit of all the hierarchy has a predetermined calendar defined.
Job Position
Optionally the job positions which correspond to the users can be indicated.
Position
Defines the job position occupied by the user.
Optionally the chatbots can be selected to work as assistants of the user.
Assistant
A user can define one or more chatbots as their assistants.
Each time the user receives a message, each of their assistants verify if they recognize that message as a command they can execute.
Each chatbot exposes the commands they can execute and defines which participants can invoke their execution.
On the other hand, those who communicate with this user can see the commands they can use by pressing the command icon on the chat window.
Delegates
The list of delegated users is indicated and the period during which the delegations of tasks is in effect.
When the user is inactive or absent then those current delegates can:
oDo the tasks assigned to the user.
oInitiate the processes authorized for the user.
Delegate of
Informs the list of users that have delegated tasks in the user and the corresponding period.
This list is dynamic and is completed at the moment of opening the user profile.
Absences
Each element of the list indicates the type of absence and the corresponding period.
During these periods of absence the mechanisms of tasks districts are activated.
Absences can be indicated considering a start and end time.
State and Expiration
User State
Indicates if the user is active or not.
An inactive user cannot enter the environment as their account is deactivated.
Expiration Date
The user account is automatically deactivated when the date entered in this property is reached. This automatic inactivation does not use the tasks delegations scheme.
This property can be used when users authentication is performed by Deyel.
Failed Accesses
Displays the number of failed accesses due to incorrect passwords.
It is incremented every time user authentication fails due to an incorrect password and returns to zero when the user authenticates successfully.
When the user exceeds the Maximum number of failed logins, his account is blocked.
Lockout Date
Displays the date and time the user's account was locked.
Used to control the Maximum lockout time for the user's account.
Licenses
Each environment of Deyel has use licenses that enable the use of licensed applications during a period of time and by a certain number of users.
In this section the list of licensed application the user can use is indicated and which type of user license they have assigned to do this.
Product
Indicates the licensed application the user can use.
License Type
Indicates the type of user license that is assigned to the user to use the product.
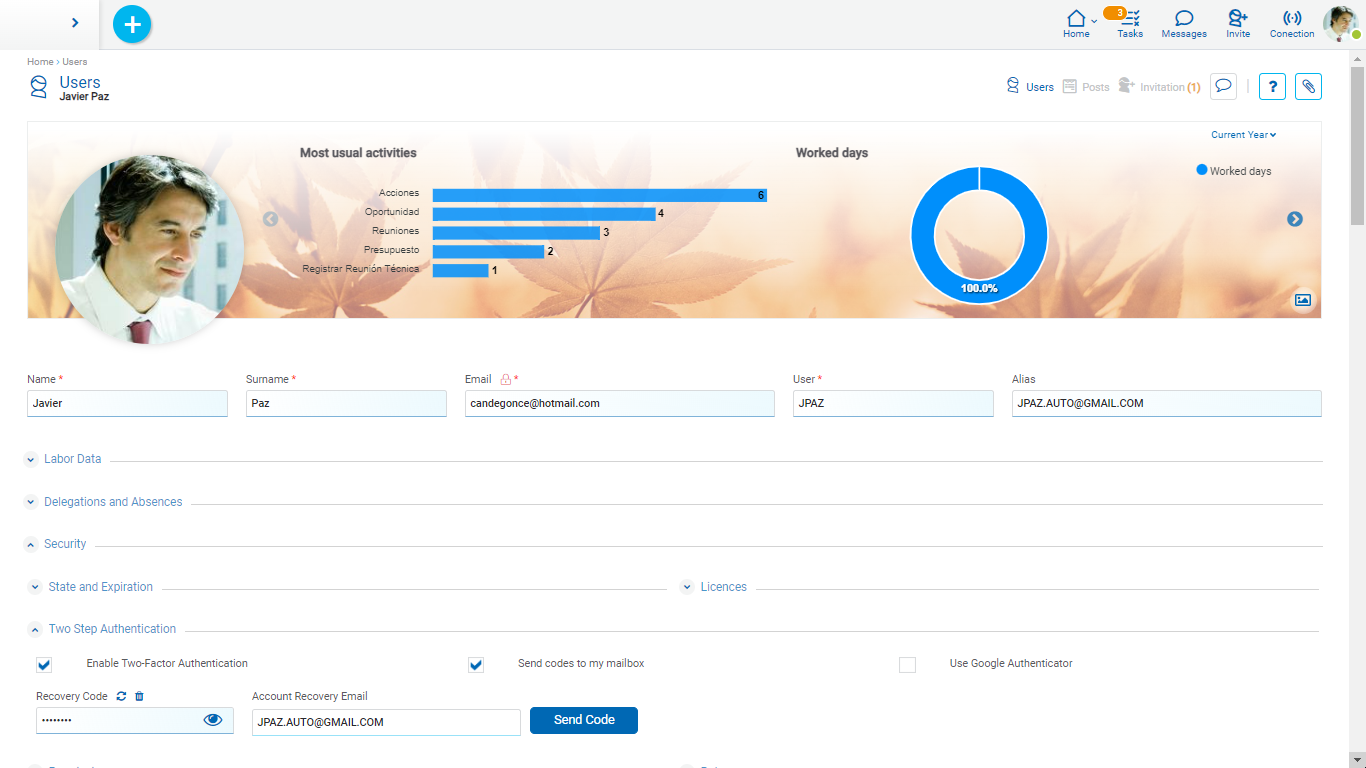
When the use of double authentication factor is enabled in the environment, this section is visualized.
If the Two factor authentication configurable property is set to “Optional”, the user can decide whether to use 2FA to authenticate. On the other hand, if the value is Mandatory, the user must configure the use of 2FA. When the user is authenticated for the first time, Deyel sends a first TOTP code by email and in turn generates an account recovery code.
For security, to prevent improper access to this information by an unauthorized person, the user is required to confirm his identity by entering his password correctly to display this information.
Enable Two Step Authentication
The user can enable or disable the use of 2FA. If it is enabled, it indicates how it want to receive the TOTP codes, being able to choose any of the following options:
Send Codes to my Mailbox
If this option is selected Deyel sends the access codes to the user's email account, which has been reported in the profile.
Use Google Authenticator
If the use of the Google authenticator is selected, a panel is displayed that tells the user how to configure said application.
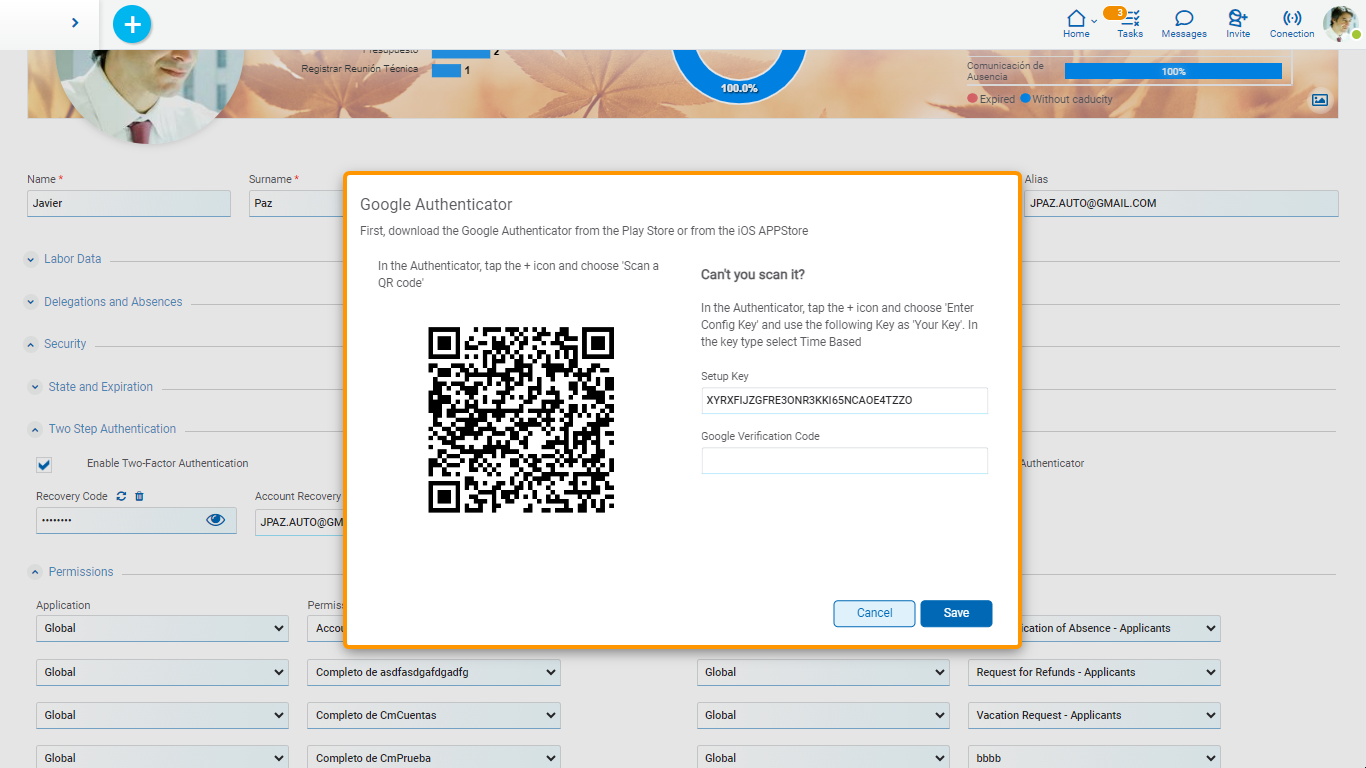
A QR code can be scanned or enter a key that is generated by Deyel.
The user must follow the indicated steps and to confirm that they have correctly installed and configured the authenticator, they are asked to enter a TOTP code generated by that application. Only when the code is verified correctly is it possible to save the configuration of the use of the authenticator.
When the authenticator has been configured and is in use, a configuration icon is displayed next to the field. By clicking, the same panel that allows to configure the use of the application on the same or another device is accessed.
The security administrator cannot access a user's 2FA settings. The user can only disable 2FA to contemplate particular situations but not re-enable it, only the user himself can do it.
Recovery Code
When the user cannot complete their two-step authentication because they do not receive their TOPT verification codes, it is necessary to offer a mechanism that allows them to overcome this inconvenience, using a recovery code.
When the user activates 2FA, a recovery code is generated. that can be consulted only by the user himself. To visualize the value, the icon ![]() must be used.
must be used.
The icon ![]() allows to generate a new recovery code, the previous one is no longer valid.
allows to generate a new recovery code, the previous one is no longer valid.
The icon ![]() allows to remove the recovery code, indicating that this mechanism is not going to be used.
allows to remove the recovery code, indicating that this mechanism is not going to be used.
On the home page, when the user needs to pass 2FA, they can request access with this recovery code.
If the correct code is reported, the 2FA is validated and the user can enter.
Account Recovery Email
When the user does not receive the TOTP verification codes and also does not remember his recovery code, another mechanism is provided for him to receive the access codes.
The user can optionally register an alternative email address, which must be different from the institutional account of the same.
To verify that the user has access to the email account, an email is sent to that address, containing a TOPT validation code that must be entered in an attached field.
When accept is pressed and there was some change in the recovery email, it is verified that the code is valid. Otherwise, it is not allowed to register the indicated email account.
Permissions
The access permissions the user has assigned are listed. Each element from the list indicates the name of the permission and the application they belong to.
In the first positions the permissions the user inherits for belonging to an organizational unit, to a role or to a job position are displayed. These elements are displayed protected and it is not possible to delete them from the list. Hovering over each of these elements, it is displayed from which object the permission is inherited.
Following the inherited permissions, the permissions assigned directly to the user are shown. When creating or modifying the user the elements from the list can be added of deleted.
First the application is selected and then the permission of such application to be assigned to the user is selected.
When permissions from a licensed application are assigned, this one must be able to be used by the user. If the application is not available in the use license of the environment, the permission is protected and it is possible to delete it from the permissions list, but not modify the element
The permission "Account Manager" can only be assigned to a unique user.
In On-Premise installations of Deyel, this permission can be assigned or removed from a user by the security administrator.
In Cloud installations, the site of Deyel must be used to change the user defined as "Account Manager".
In every installation there exists a set of predefined permissions that can be assigned to the users.
Roles
The roles the user performs are listed. The list is dynamically conformed when accessing the user profile, recovering the roles where the user or their organizational unit are actors. Each element indicates the role name and the application it belongs to.
In the first positions the roles the user inherits for belonging to a unit are displayed and then the roles where the user is an actor.
The user profile includes the following properties:
Nationality
Birth Date
Identification Type / ID Number
Phone Number / Extension
Addresses
The user can have multiple addresses, with the following properties for each of them:
Country
State
City
Postal Code
Street
Number
Department
The user profile includes information about the identity of the user in the different social networks (LinkedIn, Twitter, Facebook, YouTube y Skype).
In the case of Twitter, when publishing the corresponding adapter “Sign in with Twitter” option is enabled.
If the user has their Twitter session opened in the browser, they can grant permission to Deyel to publish tweets directly on behalf of the user. If not logged in, the user is redirected to the Twitter site to log in first.
When the authorization process is finished, from the user profile the authorized account is displayed, below their image.
Users can unlink their Twitter account in different ways:
•From their profile, clicking on the icon ![]() visualized to the right of the Twitter property.
visualized to the right of the Twitter property.
•From Twitter, the authorization for Deyel to publish tweets on behalf of the user is removed.
Additional Information
Remarks
Allows to load complementary data of the user.
This section is only available for “Smart Thing” type users.
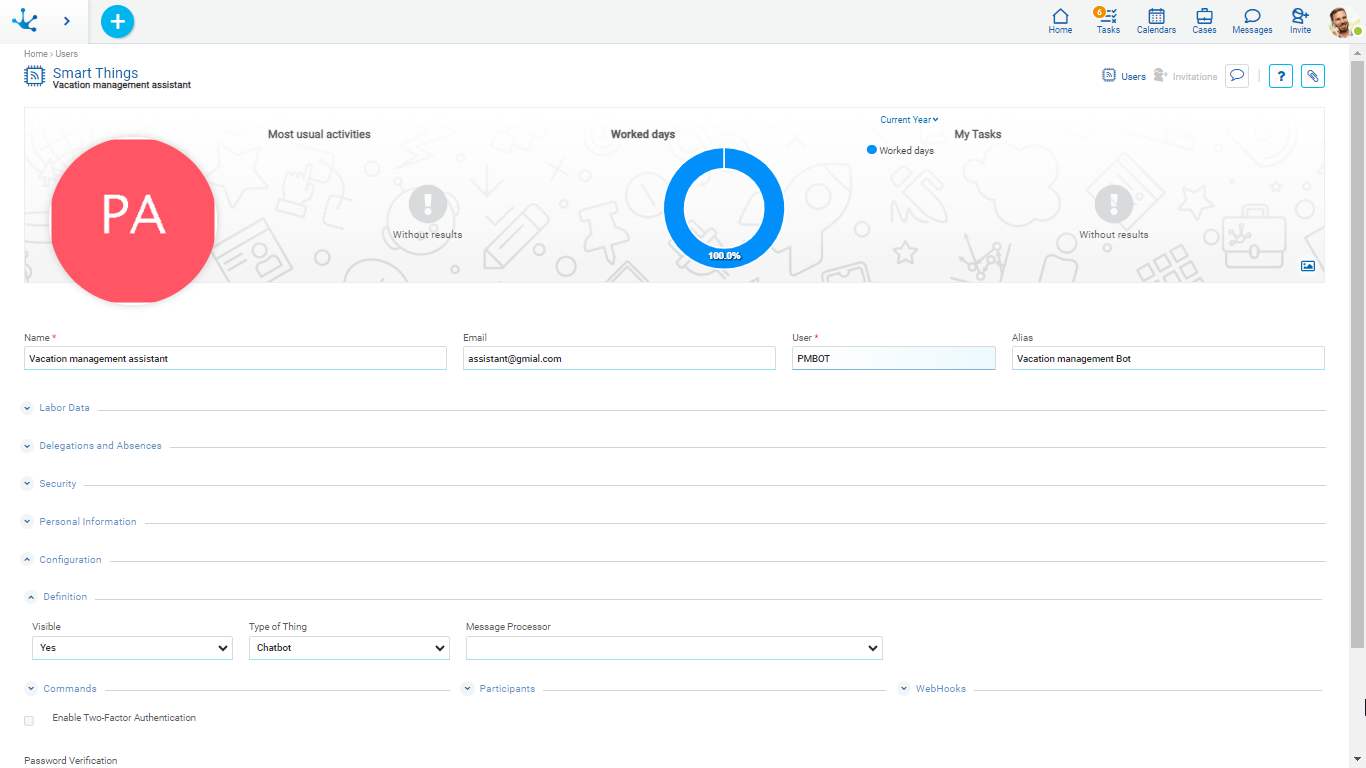
Definition
Visible
Indicates if the chatbot is visible in the users list of the business social network Tedis.
When a chatbot is not visible, it can work as an assistant, but it is not possible to send it messages directly in a chat. For “Rest API Client” type this parameter cannot be modified.
Indicates the smart thing type that represents the user. It can take “Chatbot” or “Rest API Client” values.
Message Processor
This property is exclusive for “Chatbot” smart thing type. The business process that implements the processing of the messages the chatbot receives can be defined. Each time a chatbot receives a message, it starts a case of this process to generate the corresponding response.
Commands
This section is exclusive for the “Chatbot” smart thing type and defines the list of commands the chatbot can interpret and respond to.
Executing a command implies executing the business process that implements it.
Participants
This section is exclusive for “Chatbot” smart thing type and defines the participants that can use the chatbot as an assistant.
If an organizational unit is selected, then any user from that unit can use the chatbot.
WebHooks
This section is exclusive for “Chatbot” smart thing type. Webhooks are interfaces that allow to integrate applications, that is, they allow to connect and exchange data between applications.
A chatbot can use multiple webhooks, each of them defines the URL used to contact other application, sending it data in JSON format.
When a chatbot receives a message, it forwards it to each of its webhooks.
In the upper right section the user relation with the invitations that they have done is displayed and it is allowed to show those invitations.
To make internal operations automatically, Deyel uses a predefined user called SYSTEM USER (SYSUSER).
This user is displayed in the user grid, it is not possible to modify or deactivate it and it does not require user licenses.
The initial load of the use license or its subsequent update or the execution of scheduled tasks, among others, are operations whose execution is made using this user and so it remains registered in the audit trails.
It is not possible for someone to enter the user portal authenticating as the system user. Deyel uses it only for the doing and registration of internal tasks.
