Access with Private Connections (VPN)
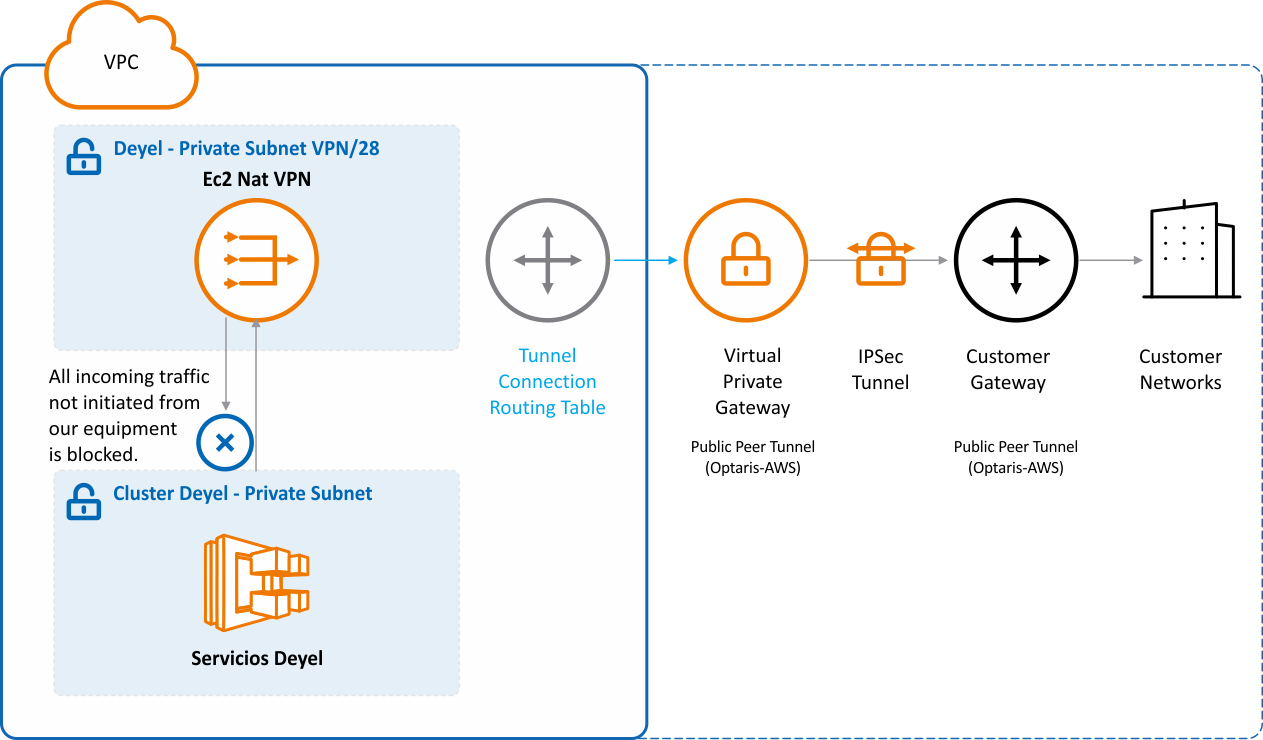
Deyel Cloud allows to establish “site-to-site” VPN connections to access from Deyel to web services located on customer’s private network servers. The VPN service includes initial configuration, connectivity testing and technical support.
To use the VPN service, the customer needs a compatible VPN device located at their corporate premises, with an assigned public IP (IPv4) address and with the capabilities to be configured using the IPsec protocol.
Deyel uses the AWS Virtual Private Gateway service to establish IpSec tunnels with its customers and thus enable access to its web services, for example by performing integrations when using a Rest API.
This service enables to establish a “site-to-site” tunnel between the customer and the AWS Virtual Private Gateway service of Deyel with the Internet Key Exchange version 2 (IKEv2) protocol.
The configuration of this service supports different types of cryptography:
AES 256-bit encryption, SHA-2 hashing.
Diffie-Hellman groups:
Phase 1 can now use DH groups 2, 14, 15, 16, 17, 18, 19, 20, 21, 22, 23, 24
Phase 1 encryption algorithms AES128, AES256, AES128-GCM-16, AES256-GCM-16
Phase 1 integrity algorithms SHA-1, SHA2-256, SHA2-384, SHA2-512
Phase 2 can now use DH groups 2, 5, 14, 15, 16, 17, 18, 19, 20, 21, 22, 23, 24
Phase 2 encryption algorithms AES128, AES256, AES128-GCM-16, AES256-GCM-16
Phase 2 integrity algorithms SHA-1, SHA2-256, SHA2-384, SHA2-512
Customer Data
•Customer Gateway: Public customer Ip where to establish the tunnel.
•Local Customer IPv4 Network Cidr: (Destination network/IP of the customer to connect privately).
•Pre Shared Key: To establish encryption.
Deyel Data
•Outside IP Address: Public IP address of Deyel provided by AWS for "tunnel 1-2", from where the tunnel is established.
•Local IPv4 Network Cidr: Private network/private IP within the VPC where the customer receives connections privately *Network/IP of the EC2 Nat-VP.




