Multiple Factor Authentication
For the native and custom authentication methods, it is possible to use a second authentication factor called 2FA, based on the input of TOTP keys (Time-based One-Time Password algorithm).
When the user successfully authenticates with his username and password, he manages to pass the first authentication factor. Immediately, if that user has activated the double authentication factor, they must overcome it by entering one of these TOTP keys.
The Administrator from Deyel can enable or disable the use of the environment variable 2FA in the installation and each user can configure how to use such variable to access the portal.
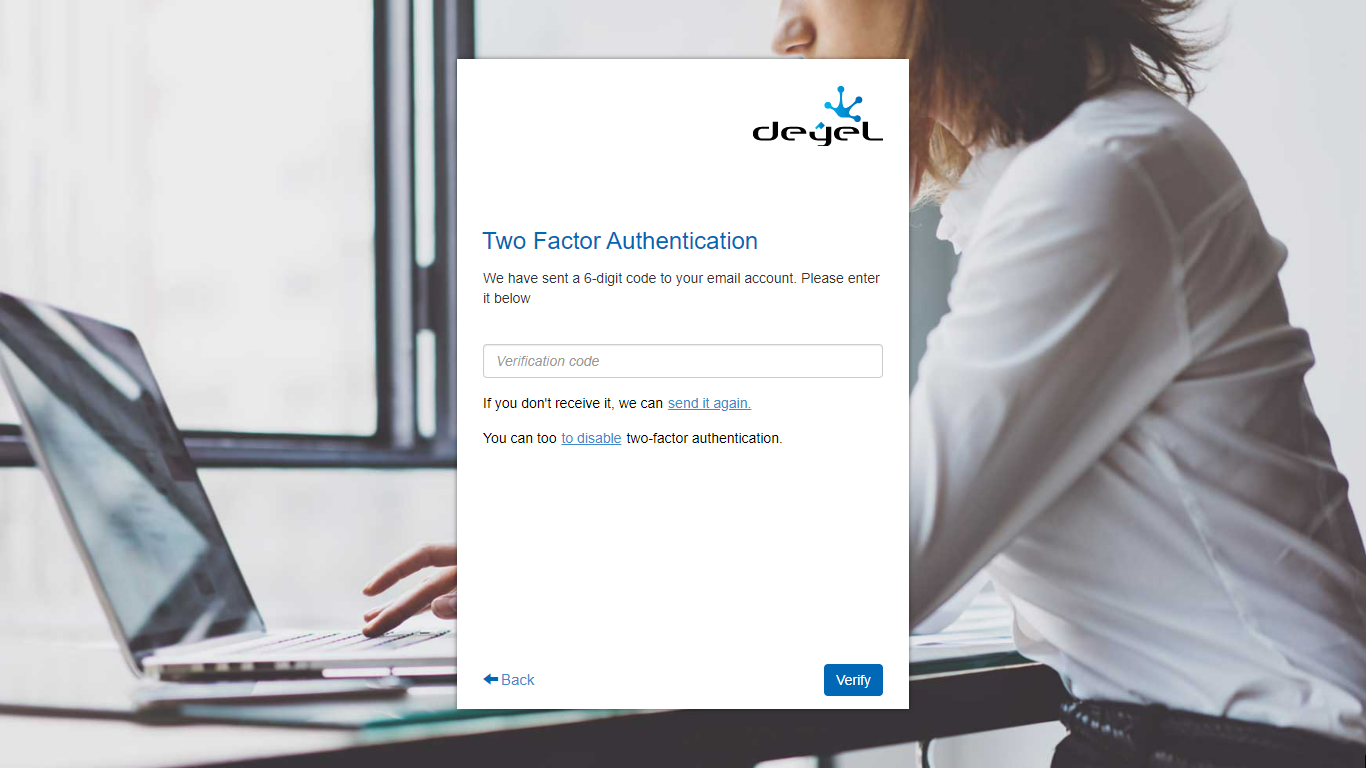
When the user configures:
•using Google authenticator can enter the verification code that the authenticator generates. It is shown as the first alternative to avoid sending emails to the user.
•the verification codes to be sent to their institutional mailbox, they receive a new code in it.
•an alternative account to receive the verification codes, receive a code to the account recovery email.
•that wants to use the recovery code and the code entered is correct, the 2FA is validated and access is allowed.
By pressing the “disable” option to deactivate two-step verification, the user is asked to confirm the operation. Once confirmed, the following message is received:
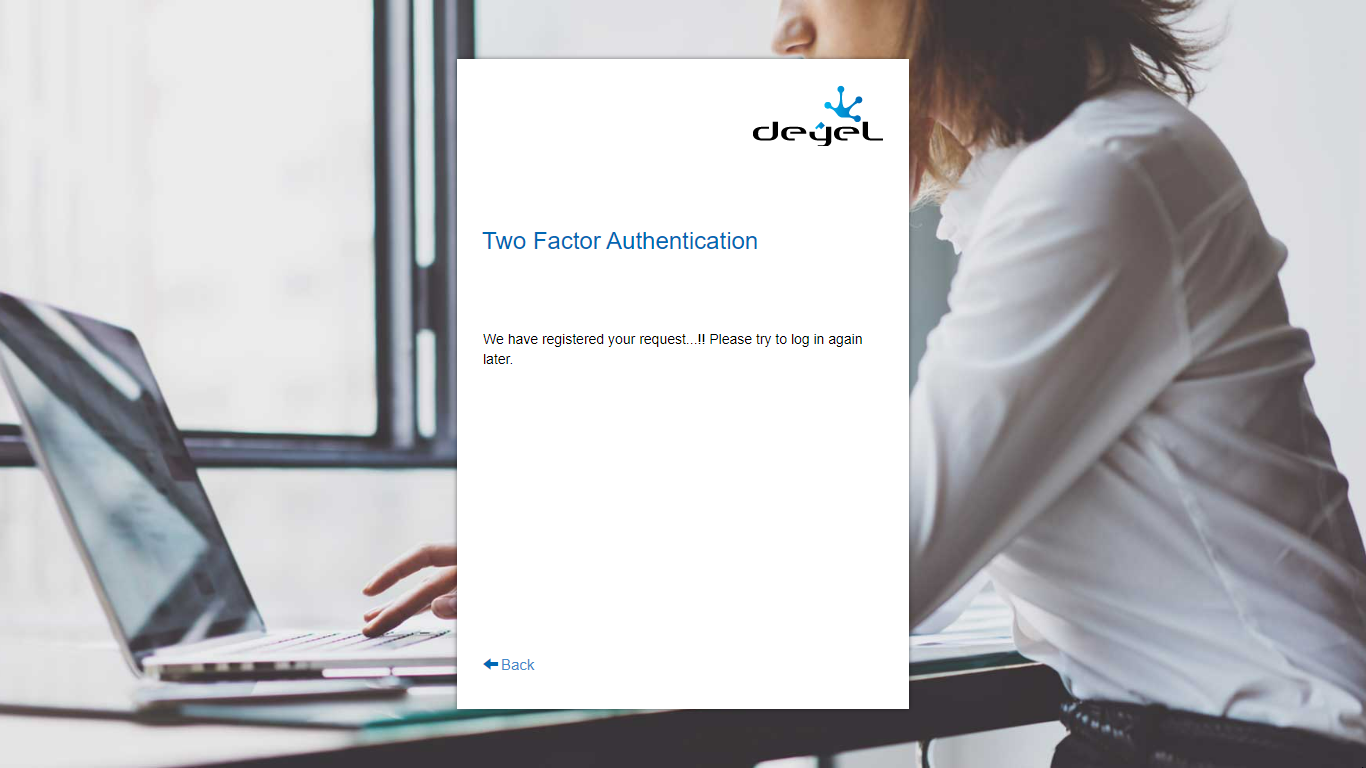
And the administrator receives a request to disable the use of 2FA for that user, which is done by accessing the user's profile and modifying its configuration. These are manual user management procedures that can take time, so the applicant is prompted to try to identify themselves later.




